Tor, This is one of the safest browsers on the Internet. In this topic, we are going to share with our readers its working process and how you can use this browser to hide your online presence.

History of Tor:
History of the Tor browser or you can call it as Onion Router was started at 1990’s. This software was created at United State Naval Laboratory. US Navy had created this software to create the more secure encrypted connection on the internet. In its official logo, you can easily see the onion with the multiple layers. This describes when you do want to surf the internet first it will connect you multiple layers before connected to the final IP.
Why Using Tor:
Most of the time this browser is used for hiding the online identity. Tor is also very much famous for accessing the dark web. Without this browser, dark we can’t be accessed.
Tork Working Process:
The working process of the most famous browser like Mozilla Firefox, Google Chrome, Safari is totally different from Tor, when you are browsing the internet on these browsers they will connect you with ISP and after that, they will connect you with the final relay. So the website which you do want to visit can easily know your IP address.
But Tor work process is totally different. When you want to surf the internet with Tor, it will create a most secure network for you. First, it will create a connection with your ISP and after that, before connect to any web server, it will create the most secure node layers. So if you want to visit any of the websites on the Internet it will not share your actual IP address with the website owner.
Below is the Tor working process how it can create the securely encrypted layer for you. For eg, if someone like Alice wants to communicate with the Bob. It will send him through multiple Tor node.
Fig. 1
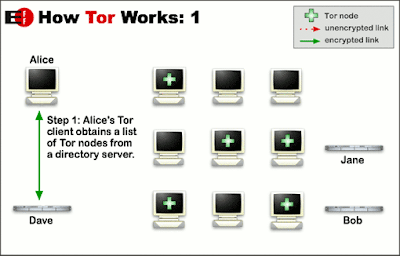
When Alice connects with the one by one multiple relays the interesting thing is, no one relay won’t be able to know Alice actual IP address. This process will continue works and will send Alice to the final relay. These all rely are encrypted by 128-bit encryption. so don’t worry. After that, it will connect to the final node. Be aware, the final node is not encrypted. It’s difficult for an attacker to get in access to the final node. But maybe he can crack it.
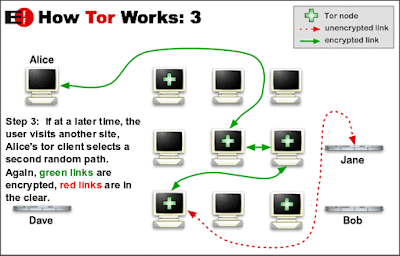
Fig. 2

In the below image clearly mentioned connection go through green line is encrypted but the red link is unencrypted. So be aware of that.
Fig. 3
Instruction Before Tor Access:
- If you think that your online presence fully protected by this browser, then you are wrong. Because the final node is not secure if someone gets in access the final node he can easily track you. For this issue do one thing, connect your system first with the VPN. It will create the more secure anonymous network.
- If you want to make a most secure network in Tor, do one thing, set security level high it will disable all java scripts of the website which you do want to visit.
- Don’t add the extensions in this browser.
- Don’t maximize the window while accessing the Tor.
- Make a sure your internet connection speed should be higher. Because when it will connect you with the multiple relays your internet speed will going to slow.
It will create one issue when you will disable java scripts. Most of the website, like Google doesn’t allow you to visit their website without java scripts. These are the few things you need to keep in mind before you do want to access the Tor network.
Nice browser but I want hacker for learn how to hack??? You r hacker
Not safe for me to get to our deep page
I wanna join the anonymous group, how can I join
you don’t you get asked
I would like to get asked.
your achievements ?
Vc quer se juntar á nós?
Ok
Vc não pode se juntar ao Anonymous
Vc precisa ter a mesma ideia que eles
Pesquise no YouTube Como onirse a nós lá vai aparecer
you can’t. you are the worst hacker ever. my tractor is a better hacker than you. go find a baby hacking cult
It’s not a group. And btw anonymous, stfu. We are friendly here. Go to hell, kid.
Even we also won’t be able to recognize other anonymous members without the mask. Maybe now you know what actually anonymous group is. If we know other members of anonymous its means there is no meaning of anonymity. The anonymous concept was started for hiding your identity from other people. You won’t be able to join the anonymous group because there is no headquarters of anonymous which controlled every operation of anonymous.
If you really want to join the anonymous do one thing, call yourself anonymous. You’re in. You can purchase guyfox mask from the shop or online store. This is the main identity of the anonymous member. Now you’re the member of the anonymous group.
you don’t you get asked
Does TOR work with Norton?
Yes,
It does work with Norton.
My entire life ive always wanted to be in something secretive. Like anonymous, to just help ppl. I sound like i want to be a spy but no, not really. I just want to be a hacker to delete mean stuffs online and fake accounts and jus do extrodinary things. How can i do dat?
when i download tor then any member of this website has a capacity to track me.
Very nice.and thank’s for anonymouse 🙂
I’m crazy
can somebody really hack my bank account really do not believed that
Of course they can
It’s just a bunch of numbers in a web, if they can hack account, phone numbers, passwords, etc they can hack the numbers of your account
But I don’t think they will do it
Anyone willing to hack a WhatsApp account for me?
I WILL HACK U ALLYOUR SOC IS ^^^:^^^:^^^^
We need to talk I’ll wait…
We need to talk
Im writing a romance novel/thriller. My main character is a hacker and so are the bad guys. Problem is, I dont know anything about anything. I need to do just enough research to make the novel believable. Is someone willing to help me a bit?
learn how to do it yourself, that’s the secret to life my friend, trust no one but yourself, if you want something done do it yourself because you are the only one that wants what YOU want done done.
Sir mujha bhi ek hacker bana hai please help me sir
Basically you need to prove yourself worthy, anon will pick up on interesting things you do, and then watch you, if they think you worthy (I’d imagine after some seriously deep searching in to your history) then you get an invite to say lvl1 (a Labourer on a construction site)
THE fact that you are asking to join says that you are not worthy
No I am not Anonymous, I am a forward thinking person who understands how things May work
That was what someone from Anonymous would answer 😉
i want join with you
please help me
can i join ?
I want to be a part of Anonymous…can you help me…?
This seems so easy ,but how did u create it ? how did you create the directory server
ok shirihari i will mesg shortly
With
I went through a lot of troubles getting a trustworthy hacker. It was not easy. I want you guys to
save yourselves the troubles I went through. Allow me to recommend someone to you. He is none other
than wisetechhacker. He is a damn fine hacker. Reach him on (wisetechhacker @gmail.com)
Que programas de antivirus estan reportando tu informacion personal al servidor del que provienen o solo estoy paranoico comienzo a pensar que estos amigables programas de proteccion realmente estan haciendo mas qie escanear y proteger tus archivos alguien a sentido o visto algo estraño con el antivirus AVIRA o algun otro
Not all of anonymouse member are Black Hat, Some member White Hacker.Respect
Can we use more than one VPN for security
tor is safe but i’m not risking it
I don’t understand It
Nothing about nothing
Cogito ergo sum
F. Nietzsche
Disaisse metabólic rares
I can help if you have problems in Spain , come here, to Madrid
Moi je veux que anonymous m’apprendre à pirater des sites internets